User administration and access protection for structure blocks
(available on demand)
1 General
Accessing selected structure blocks and programming system functions (edit, download, etc.) can be limited to certain users or user groups over the user administration.
Know-How-Schutz für ausgewählte Software-Module
-
Know-how protection for selected software modules
-
Protection against modifications of security functions
By using the user administration, iCon-L can also be forwarded to qualified service staff. That way the user does not have to worry, that the software could be manipulated or destroyed.
The maximum rights are still limited by superimposed protection systems, f.e. by dongle settings. Name, login password and rights as well as the passwords for the structure block access are saved in the accounts of the users.
| Type | Description |
|---|---|
| Admin | The admin can call all functions of the programming system except for the command „free access“. Furthermore he can add, edit and delete other users. |
| Developer | The developer can call all functions of the programming system, except the command “free access”. |
| User | For users, the set of functions of the programming system is limited to the viewer version. Furthermore commands to create new projects for offline programming as well as loading and saving connector parameters and the parameter list are deactivated. |
| Guest | Additionally to the limitations of the user, guests cannot call the commands “download”, “simulation” and “parameter download”. |
Name, login password, rights and the passwords for the structure block access are saved in the accounts of the users.
All users can change their own accounts except for the rights settings. The rights settings can only be adjusted by another admin. By that it is always secured, that there is at least one admin.
Admin rights (limitations)
Admins can change additional settings of other users, add new ones and delete others except themselves. The settings options for other users are limited to the name, the rights and assigning a new login password. The admin CANNOT read or change the passwords for accessing the structure blocks. With this limitation, accessing someone else’s secured structure blocks is denied for admins, too.
Access
To access user accounts, the extended IACCESS.DLL allows an interface function for the “Tools” menu. After the configuration, the function can also be called over the corresponding tools list. For admins, a dialog with a list of user accounts opens. With the buttons, new accounts can be created, existing accounts can be edited and deleted and the list can be updated. Users with less rights can directly get to the dialog with their account settings. The changes on the accounts are directly written in the binary file after closing the dialog.
The possibility to use several instances in the programming system at the same time, makes the permanent saving of changes necessary. Furthermore, the settings of the logged-in user, saved locally or in the file, are also checked for changes when opening the dialogs with the user list, a user account, or the password list for structure blocks. If necessary, an update is being recommended.
Especially critical are changing the name or rights of users, who are logged-in in another instance of the programming system. Based on the name, the corresponding account settings can be found in the file. An immediate adjustment of the programming system to the new user rights is only possible in exceptional cases. That is why the “externally changed” user is denied access to their own and other user administration data, unless the programming system is restarted and the user logs in again.
3 Use of user administration
Login
When starting the programming system, the user has to login with their name and password. The name of the user, who accessed the system last is proposed in the field. After typing in the wrong name or password 5 times, the login dialog closes and the programming system shuts down.
After successfully logging in, the programming system can be used.
Default settings
At the moment, the default account has the name “Administrator” and the password is left free.
Call User Manager as Admin
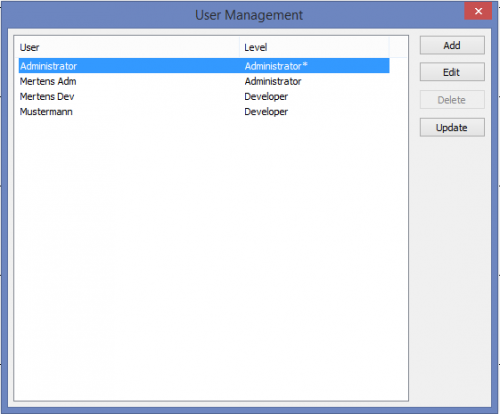
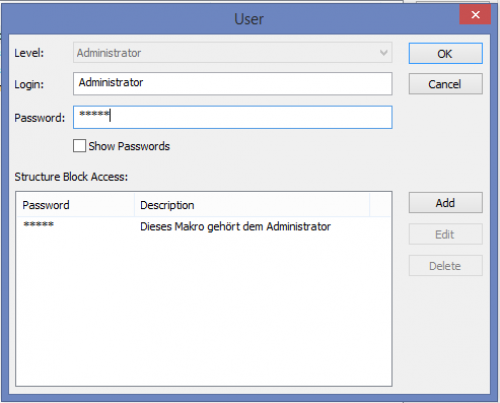
If you are logged in as admin, you can see the list of all users registered for the programming system in the User Manager.
-
The admin cannot delete themselves (deactivated delete)
-
The admin can configure themselves
-
Change login password
-
Create, change and delete passwords for accessing and securing structure blocks
The password list has two functions
- If I would like to protect a structure block, I can select a password from the list.
- If I would like to open a structure block, I have to enter the password given to me.
4 Requirements for accurate processing
The accounts of the users are saved in an encrypted binary file. The user administration always requires a correct data basis with at least one administrator.
5 Access protection for structure blocks
The access on programs and macros is protected by passwords. The configuration for each user is visible and can be edited by admins and developers at any time. One user can define up to 10 passwords, which they assign to programs and macros in structure block design. As in the data structure for structure blocks only one Word value each can be assigned for the access protection, checksums are calculated from the passwords and implemented in the data structures. The value 0 is reserved for free access. All passwords, which make this checksum, are invalid. Obviously, with 65,536 checksums it might happen that two passwords have the same checksums. So, from only four capital letters (A-Z) 456,976 different passwords can be created, which means at least 6 combinations make the same checksum.
If a program or macro contains a Word value other than 0, it is secured. Before executing the commands “edit” and “design” as well as level change during run mode, the list of passwords of the logged-in user is checked. If none makes the needed checksum, access is denied. Furthermore, blocked structure blocks cannot be exported nor printed out. The commands “delete”, “rename” and “copy” for structure blocks can also be called with missing access rights.
Blocked structure blocks are marked in the project tree by yellow symbols for the logged-in user. Macros without access protection are also blocked in run mode, if they are implemented in a program or macro, which cannot be accessed. After creating a password, a lock is shown next to the table headers “Inputs” and “Outputs”, on the worksheet for the design. It marks the secured structure block. After removing the password protection, the symbol vanishes.
When working with the dialog “structure block access”, which can be called over the design toolbar, the list of passwords can be changed and the structure block can be assigned a new password. After clicking on “OK”, the marked password is assigned to the structure block and the list is saved. If no password is selected, the structure block can be accessed freely. When cancelling, the dialog is closed without making changes of the previous password assignments. When changing the list, a dialog opens to ask whether the changes should still be saved.
To make sure, that newly created structure blocks can always be accessed, the Word value “0” is saved in the design template in iCon-L and test.con for access protection. After calling the command “Define as design template” for a protected structure block, the named value is contained. Furthermore, the structure block data is not changed by the command “Reset design template”. Password protection will remain.
By deleting or changing the password, the user can deny access rights for themselves. Worksheets of blocked structure blocks that might be opened, are automatically closed during editing and in run mode an unblocked level is shown. In blocked structure blocks, no editing and design operations can be undone.
6 Patch
The available patch for iCon-L 6.0.0.0 R1 contains modules and configuration proposals for the beta version 7 for internal testing of the user administration.
The submenu “Modules” contains the changed components of the beta version. The iAccess.dll in the BIN directory contains the functions of the user administration. To deactivate the user administration, the iAccess.Default.dll has to be accessed.
As described above, a new command for editing the user accounts is needed in the menu “tools”. The submenu “Configurations” contains proposals for the global and project-specific configuration files. To keep own settings, the files should not just be copied. Furthermore the configuration files in the projects have to be adjusted.
7 Data formats
The requirement, that the user administration can be activated or deactivated, means that files with structure blocks have to be protected additionally. Project files and restore files are marked with a special identification, so they cannot be loaded with a deactivated user administration or from older versions of the programming system. Projects and restore files, which have been created without a user administration can be opened with the user administration. Furthermore, the values for structure blocks for the access protection in older projects are automatically being reset to “0”.
With active user administration, only a binary format is available for the structure block export, which differs from the one used in older versions. For import, SBX files in the familiar text format and the old binary format are supported. Without any user administration, only SBX files can be exported and imported. Therefore new commands for creating structure blocks are used, which cannot be recognized in older versions of the programming system.
